-
Notifications
You must be signed in to change notification settings - Fork 38.7k
Descriptor expansions only need pubkey entries for PKH/WPKH #15263
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Conversation
ff65689 to
11e0fd8
Compare
|
I believe the existing tests are sufficient here. |
|
utACK 11e0fd8 Nice, thanks :) |
|
Nit: the top comment of Concept ACK, I think. Just checking if I understand the rationale correctly, in the proposed descriptor importmulti : This currently doesn't import the public keys, only the scripts. That can be solved by adding Later on in the import process This in turn is relevant for That's where my brain gives up, but I'm guessing that |
That's what the code originally was, before I complained that that would make outputs to multisig participant keys marked as IsMIne.
I agree this is hard to reason about... replacing all this logic with descriptor based logic will hopefully make it more transparent and with fewer gotchas.
Right, the problem is that our only way of importing a public key does two things that ought to be independent:
If it was just the first, it would be harmless; teaching how to sign something never hurts if you don't accidentally also make unrelated things treated as IsMine. What this change does is make descriptor expansions for multisig no longer fill up the pubkeys that occur in the script. This is safe because they weren't actually needed for the first effect, and has the added benefit that when combined with the importmulti code will cause these multisig individual keys to not become watched. However, it does keep the effect that when you import say a P2WPKH descriptor, the pubkey will be expanded, and then imported, causing P2PKH outputs for the same key to also become watched. Thankfully, that is "policy compatible" - anyone able to spend a P2WPKH output would also be able to spend the P2PKH version. It's unfortunate, but not a disaster. The full solution will be descriptor based IsMine logic, where we can exactly control what is treated as ours. |
Is this import also what causes Anyway, utACK 11e0fd8 |
|
@Sjors Similar but different effect. For private keys we rely on the "ImplicitlyLearnRelatedScripts" function to know how to spend P2PKH/P2SH/P2WSH (in memory) for every private key in the wallet. For public keys, the reason is that we only have one record (watch only keys) in the keystore for both watching and solving public key related scripts. |
…WPKH 11e0fd8 Descriptor expansions only need pubkey entries for PKH/WPKH (Pieter Wuille) Pull request description: Currently, calling `Expand` on a `Descriptor` object will populate the output FlatSigningProvider with all public keys involved in the descriptor. This is overkill, as pubkey entries are only needed when the lookup of a public key based on its hash is desired (which is the case for `pkh`, `wpkh`, and `combo` descriptors). Fix this by pushing the population of pubkey entries down into the individual descriptor implementation's `MakeScript` function, instead of doing it generically. This should make it easier to implement #14491 without importing P2PKH outputs for the individual public keys listed inside a multisig. Tree-SHA512: 5bc7e9bd29f1b3bc63514803e9489b3bf126bfc177d46313aa9eeb98770ec61a97b55bd8ad4e2384154799f24b1bc4183bfdb4708b2ffa6e37ed2601a451cabc
b5d3987 Take non-importing keys into account for spendability warning in descriptor import (Pieter Wuille) 6e59700 Import all origin info in importmulti; even for non-importing pubkeys (Pieter Wuille) 9a93c91 Keep full pubkeys in FlatSigningProvider::origins (Pieter Wuille) Pull request description: This fixes #15743 and #15742. Since #15263, pubkeys are no longer imported for non-PKH (or WPKH, or any wrapped form of those) outputs, as that would incorrectly mark outputs to single-key versions of multisig policies as watched. As a side effect, this change also caused origin info not to be imported anymore for multisig policies. Fix this by plumbing through the full pubkey information for origins in FlatSigningProvider, and then importing all origin info we have in `importmulti` (knowing more never hurts, and additional origin information has no negative consequences like importing the pubkeys themselves). ACKs for commit b5d398: MeshCollider: utACK b5d3987 Tree-SHA512: 37caa2be8d01b8baa12f70a58eaa7c583f5f0afbe012e02936dd8790dc5dc852f880b77258b34ddb68cae30c029585f2d1c4f5d00015380557a1e8b471e500f3
Summary: This is a backport of Core [[bitcoin/bitcoin#15263 | PR15263]] Depends on D6198 Test Plan: ninja all check-all Reviewers: #bitcoin_abc, Fabien Reviewed By: #bitcoin_abc, Fabien Differential Revision: https://reviews.bitcoinabc.org/D6200
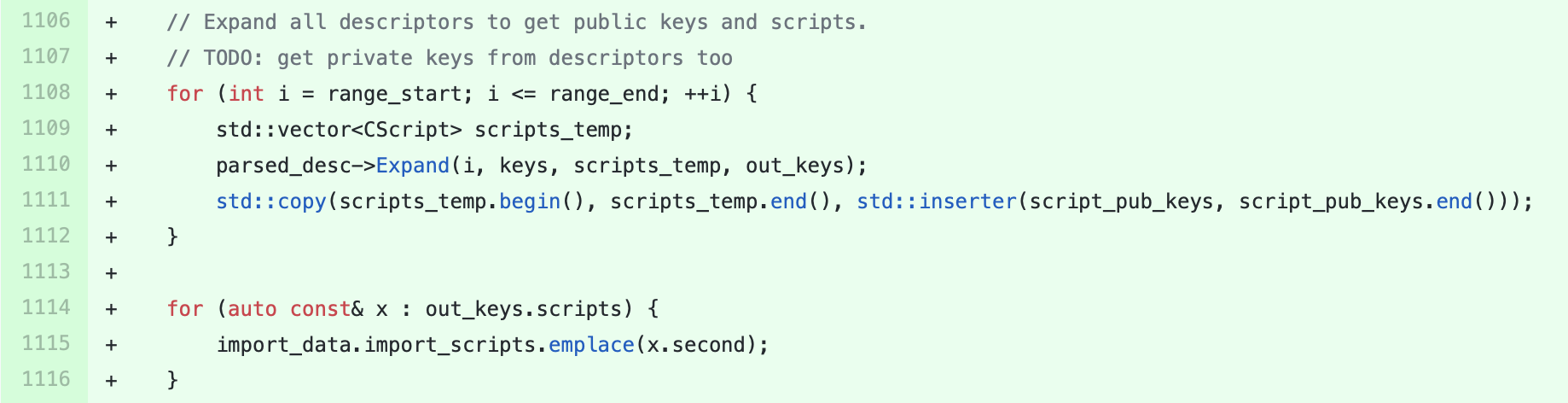

Currently, calling
Expandon aDescriptorobject will populate the output FlatSigningProvider with all public keys involved in the descriptor. This is overkill, as pubkey entries are only needed when the lookup of a public key based on its hash is desired (which is the case forpkh,wpkh, andcombodescriptors).Fix this by pushing the population of pubkey entries down into the individual descriptor implementation's
MakeScriptfunction, instead of doing it generically.This should make it easier to implement #14491 without importing P2PKH outputs for the individual public keys listed inside a multisig.