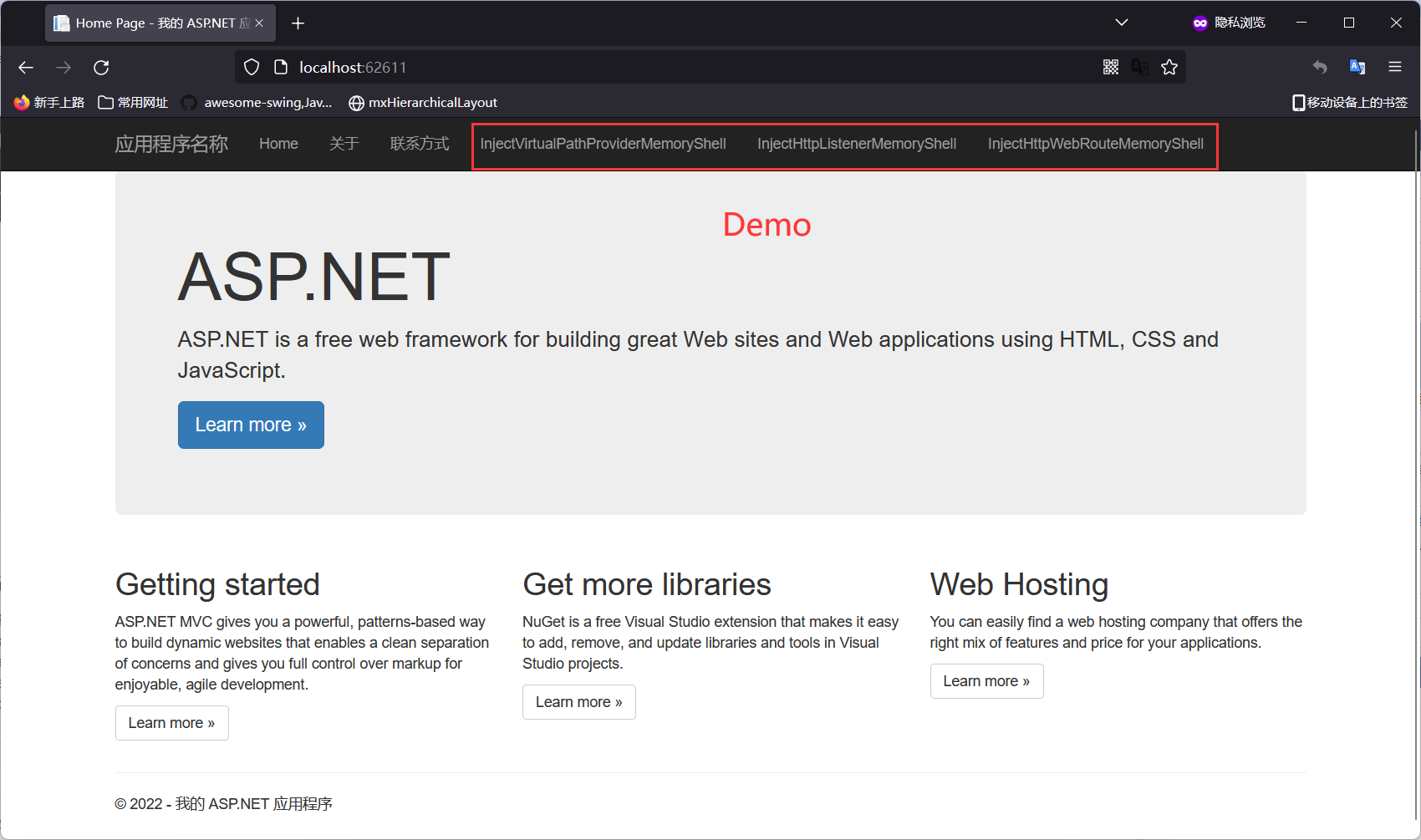
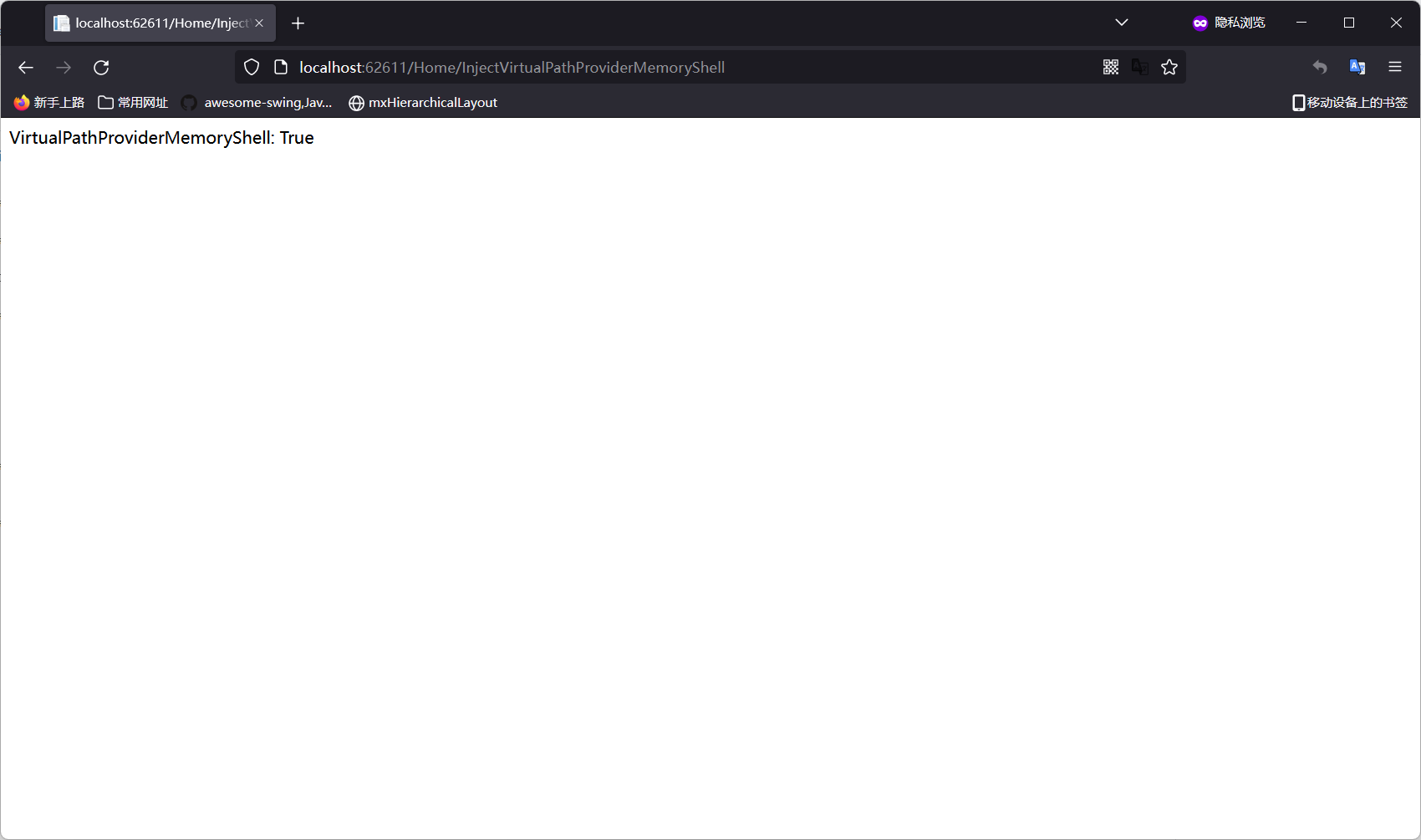
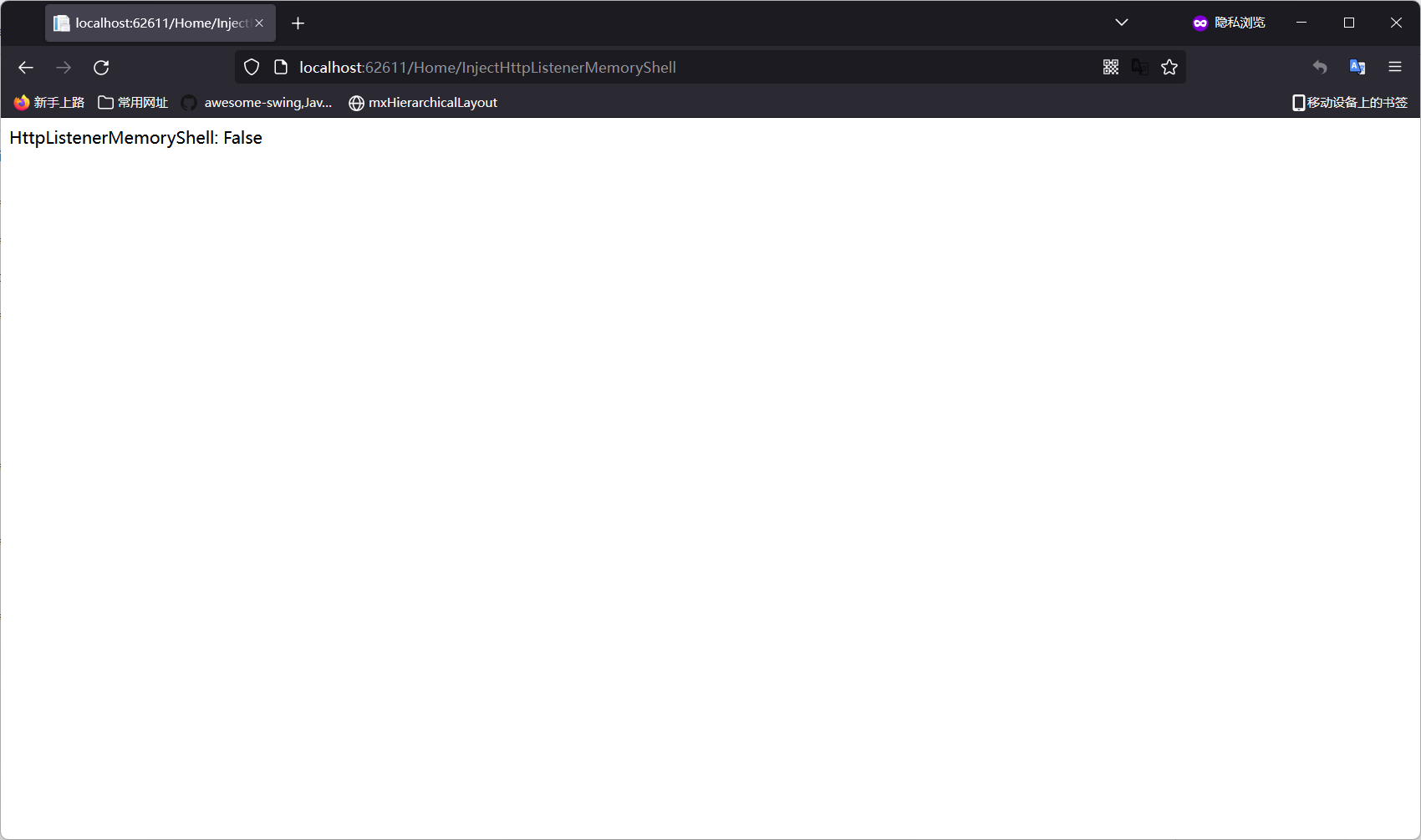
当目标存在反序列化漏洞或其它漏洞,我们可以通过加载此项目的类来获得无文件的内存Shell
姊妹项目(Java 内存Shell):https://github.com/BeichenDream/GodzillaMemoryShellProject
-
普通的ASP.NET 网站(存在aspx/asmx/ashx/soap/...)
-
ASP.NET MVC网站
-
System权限(HttpListener复用适用于所有类型)
连接时URL填写目标已存在的可执行脚本,如aspx/asmx/ashx/soap http://127.0.0.1:80/Test.aspx
连接时URL填写httpListenerURL,如http://127.0.0.1:80/godzilla/ http://127.0.0.1:80/ews/soap/
连接时URL填写目标已存在的路由,如http://localhost/Home/About